Эксперимент по сетевой безопасности 14. Настройка IPSec VPN для реализации туннельного взаимного доступа между частными сетями.
IPSec (безопасность интернет-протокола) — это открытая стандартная структура, используемая для предоставления услуг безопасности для связи в IP-сетях с целью обеспечения конфиденциальности, целостности и аутентификации источника данных. Обычно он состоит из двух основных частей: заголовка аутентификации (AH) и инкапсулирующей полезной нагрузки безопасности (ESP), которые отвечают за аутентификацию и шифрование данных соответственно. IPSec VPN использует эти механизмы безопасности, чтобы позволить удаленным пользователям или филиалам получать безопасный доступ к ресурсам внутренней сети компании через незащищенные общедоступные сети, такие как Интернет.
Общие шаги по настройке IPSec VPN на межсетевом экране Huawei следующие:
1. Подготовка
- Определить топологию сети и требования: уточнить диапазон сетевых адресов удаленных объектов и штаб-квартир.、Безопасность Требовать、Методы аутентификации и т. д.
- Собирайте информацию: включая общедоступные IP-адреса на обоих концах (или динамическое доменное имя DNS, если используется динамический IP), предварительный общий ключ (PSK), алгоритмы аутентификации и шифрования и т. д.
2. Настройте политику IKE (Интернет-обмен ключами).
- Войдите в веб-интерфейс управления или CLI брандмауэра Huawei.
- Создать предложение IKEБезопасность,определениеалгоритм шифрования(нравитьсяAES-256)、Алгоритм хеширования (например, SHA2-256)、Группа DH (например, группа 14)、Метод аутентификации (предварительный общий ключ) и т. д.
- Создать узел IKE,Укажите общедоступный IP-адрес узла, предложение безопасности, общий ключ и идентификатор узла.
3. Настройте политику IPSec.
- Создать предложение по безопасности IPSec,определение Режим инкапсуляции(транспортный или туннельный режим)、алгоритм шифрования、Алгоритм аутентификации、PFS (совершенная прямая секретность) и т. д.
- Установить политику IPSec,Предложение ассоциации IKE Peer и Безопасность,Определите интересующие потоки (т. е. сетевой трафик, который необходимо зашифровать и защитить).
4. Настройте политику IPSec IKE.
- доопределениеизIKEБезопасностьпредложениеиIPSecБезопасностьпредложениесвязанный водинрост,формаодинполныйIPSec Политика IKE。
5. Настройте обход NAT (при необходимости).
- Включите функцию обхода NAT (NAT-T), чтобы разрешить трафику IPSec проходить через устройство NAT.
6. Настройте маршрутизацию
- если необходимо,Конфигурация статических точек маршрута к одноранговой сети,Убедитесь, что пакеты данных могут быть перенаправлены правильно.
7. Проверка и проверка
- Проверьте состояние IPSec SA на странице состояния брандмауэра или используйте инструменты командной строки, чтобы убедиться, что туннель установлен и активен.
- Попробуйте получить доступ к внутренним ресурсам из клиента или удаленной сети, чтобы убедиться в нормальности соединения.
8. Устранение неполадок
- Если соединение не может быть установлено после Конфигурации,Проверьте детали конфигурации, доступность сети, журналы брандмауэра и многое другое.,чтобы найти проблему.
2. Этапы настройки
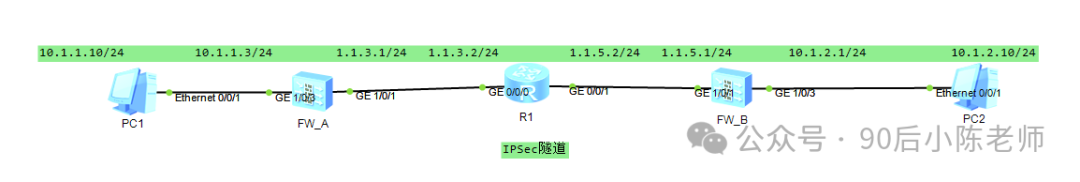
Шаг 1. Параметры сети брандмауэра А.
Имя пользователя: admin
Старый пароль: Админ@123
Новый пароль: Huawei@123
(1) IP-интерфейс
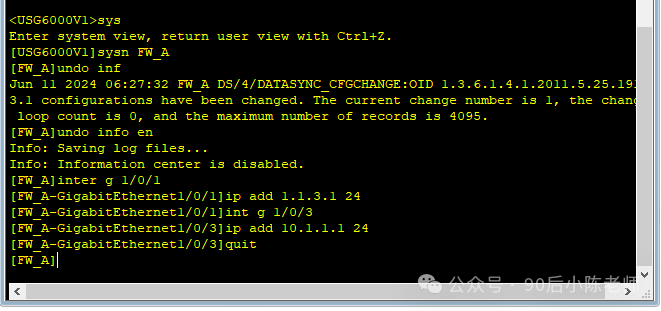
(2) Интерфейс добавлен в зону безопасности.
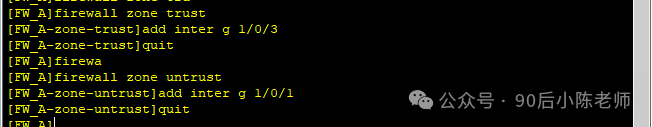
(3) Настройте маршруты к сети B и противоположному концу туннеля.
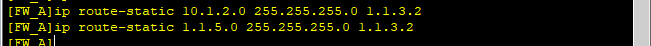
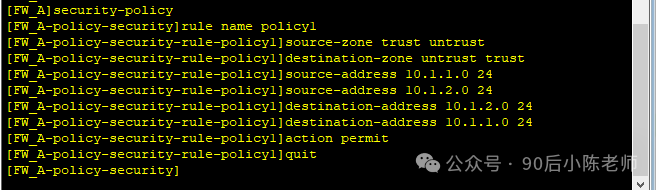
Шаг 2. Политика безопасности брандмауэра
(1) Взаимный доступ между Доверенной зоной и Недоверенной зоной.
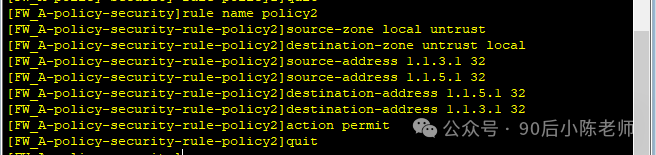
(2) Взаимный доступ между локальной зоной и ненадежной зоной.
Шаг 3. Настройка IPSec on Fire A
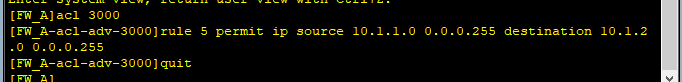
(1) Определите защищенный поток данных.
(2) Предложение IKE Safety (Брандмауэр А и B должны быть одинаковыми)
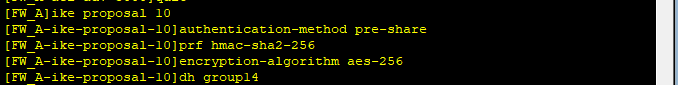

(3) Одноранговый узел IKE
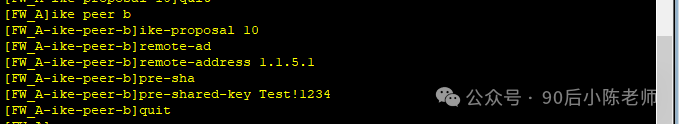
(4) Предложение IPSec Safety (Брандмауэр А и B должны быть одинаковыми)
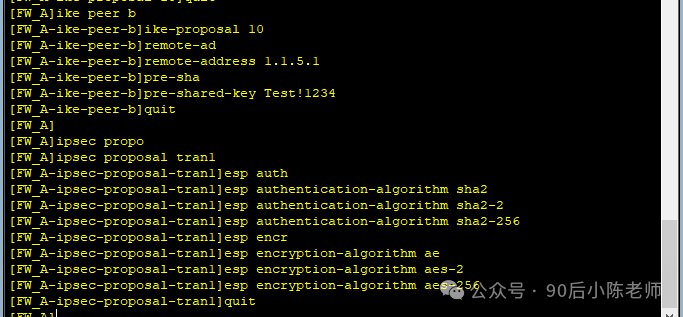
(5) ISAKMP IPSec
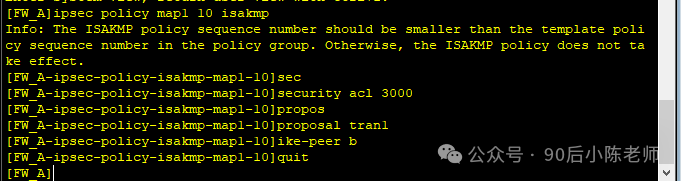
(6) Примените IPSec на интерфейсе.

Шаг 4. Настройте брандмауэр Б.
(1) IP-интерфейс
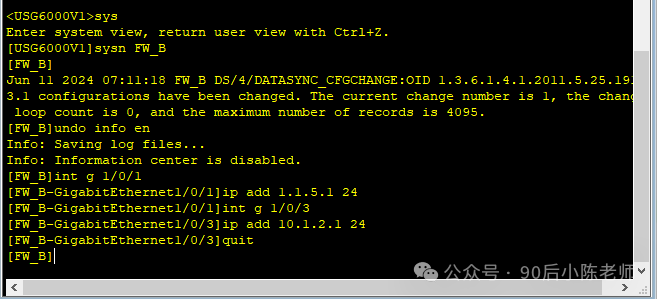
(2) Интерфейс добавлен в зону безопасности.
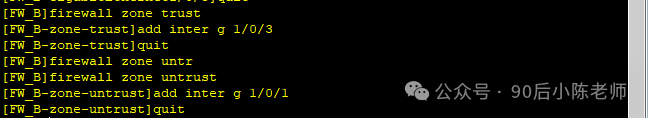
(3) Маршрут к сети А и противоположному концу туннеля.
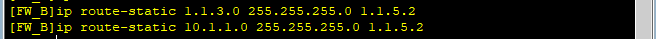
(4) Стратегия безопасности
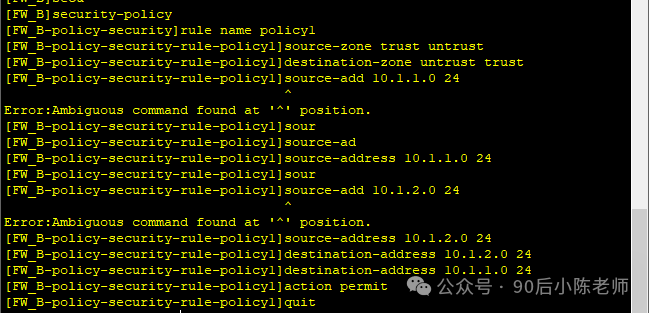
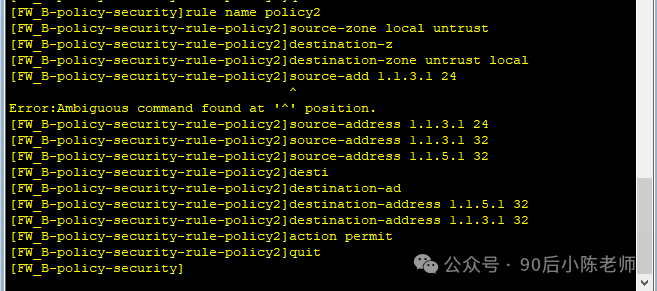
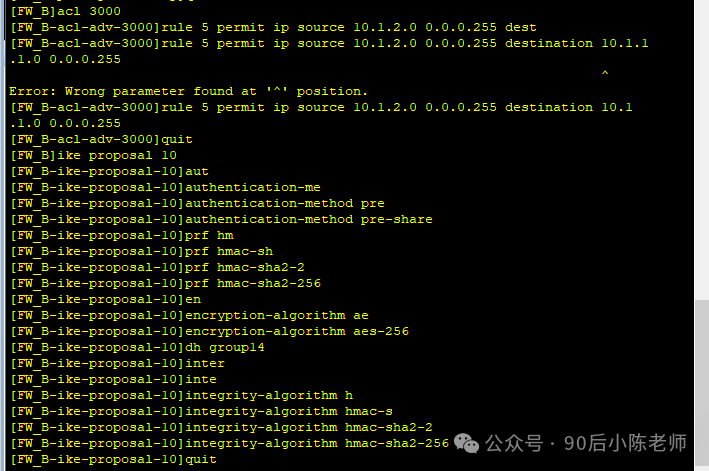
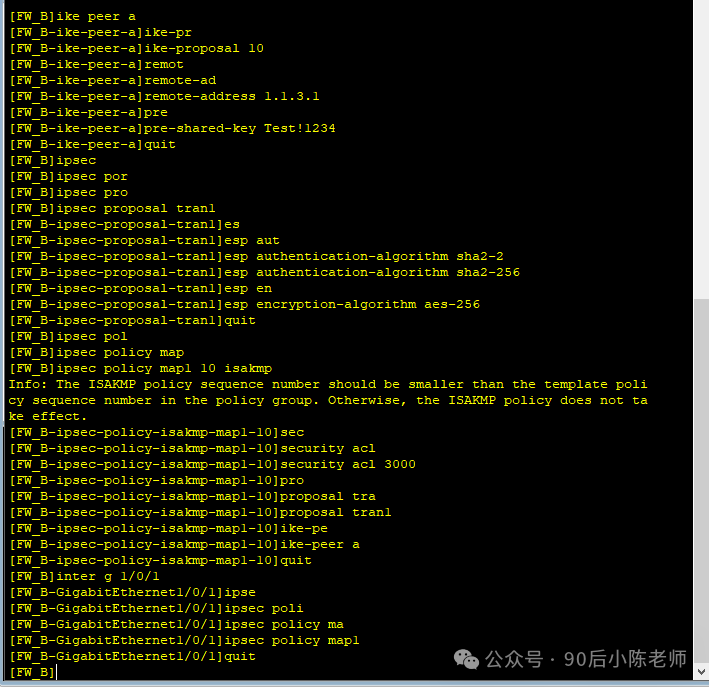
(5) Информация, связанная с IPSec
Шаг 5: Другие устройства
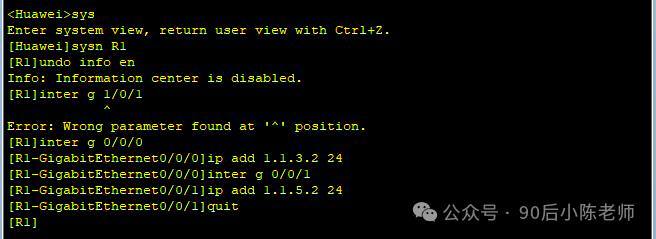
(1)Маршрутизатор Р1
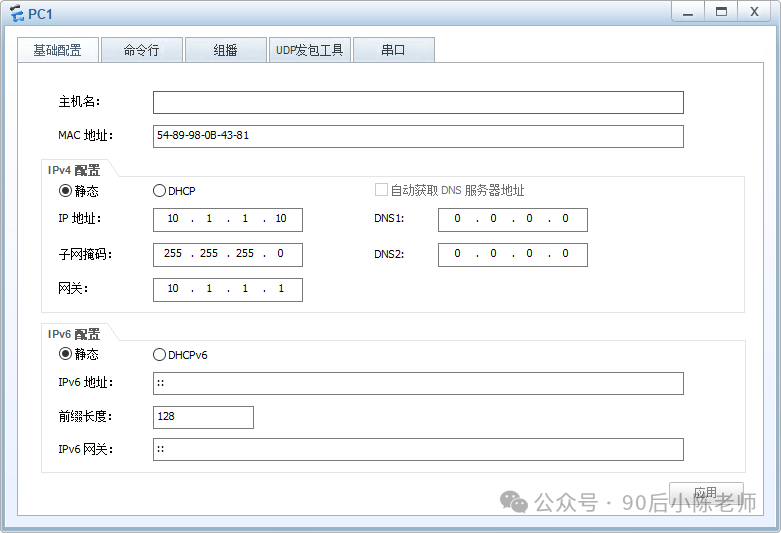
(2) ПК1 и ПК2
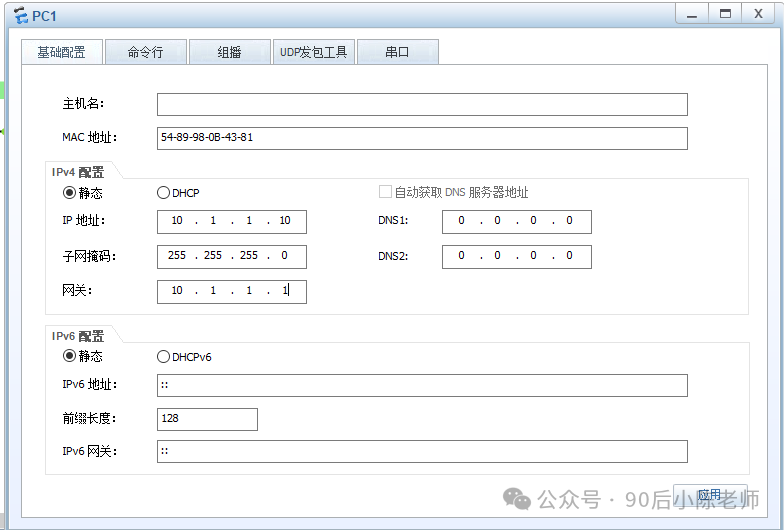
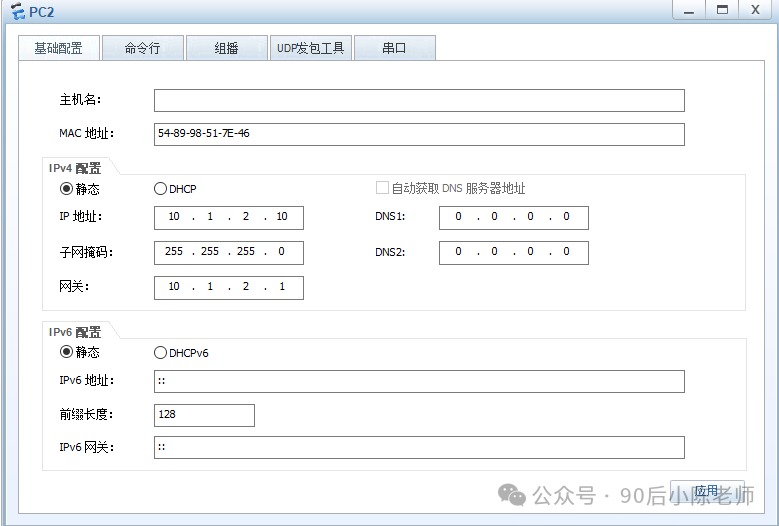
Шаг 6. Проверка и отладка
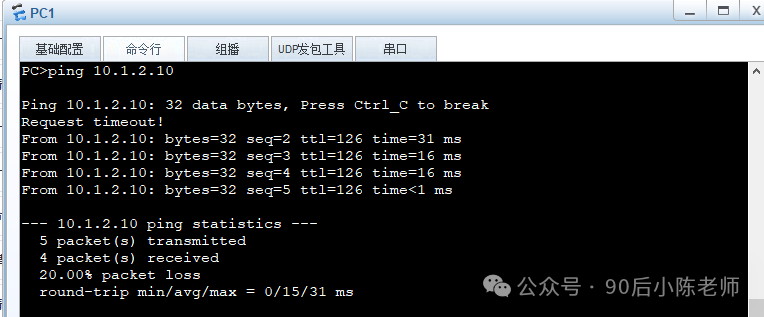
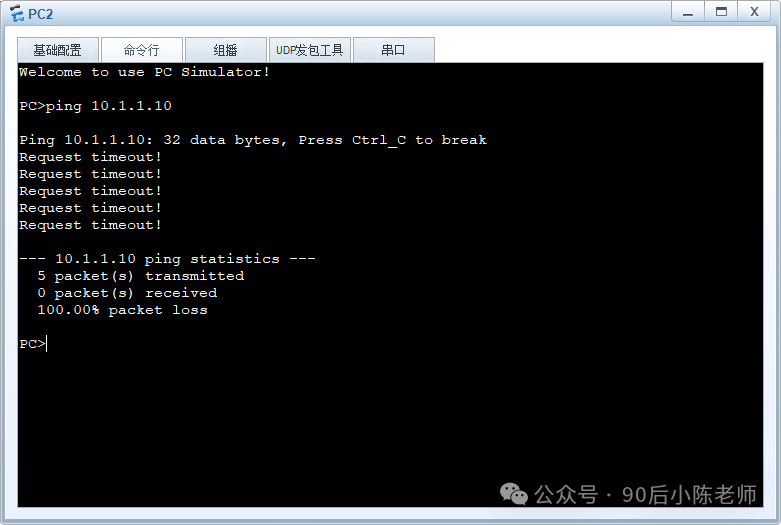
(1)PC1 ping PC2
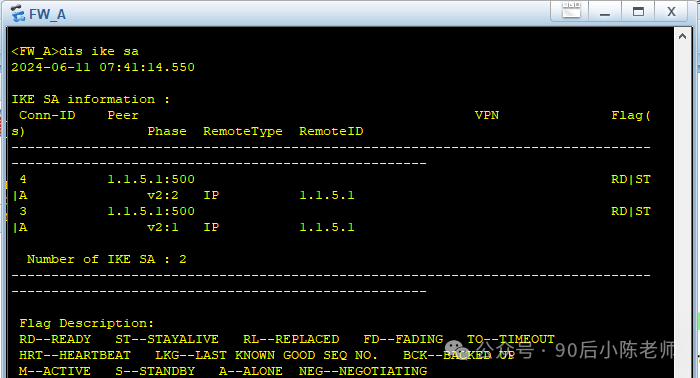
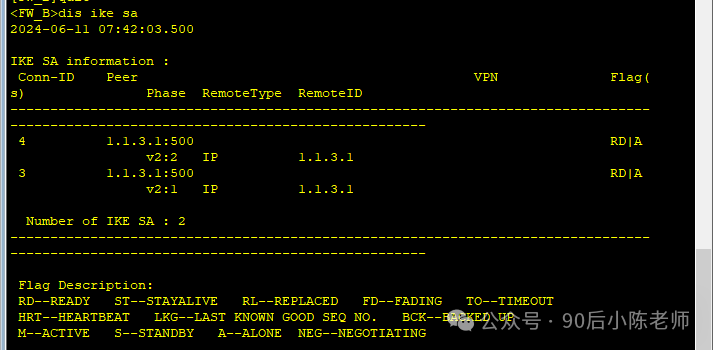
(2) Посмотреть IKE SA
Брандмауэр А
Брандмауэр Б
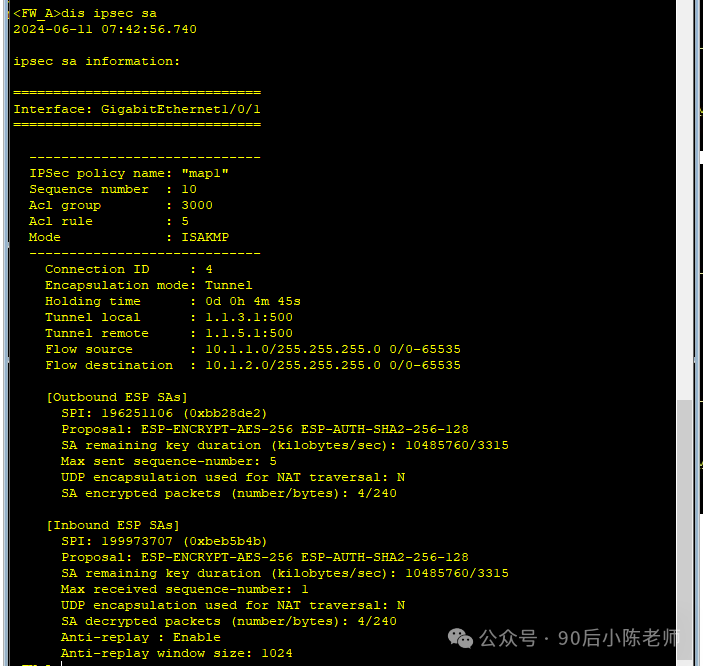
(3) Просмотр IPSec SA
Брандмауэр А
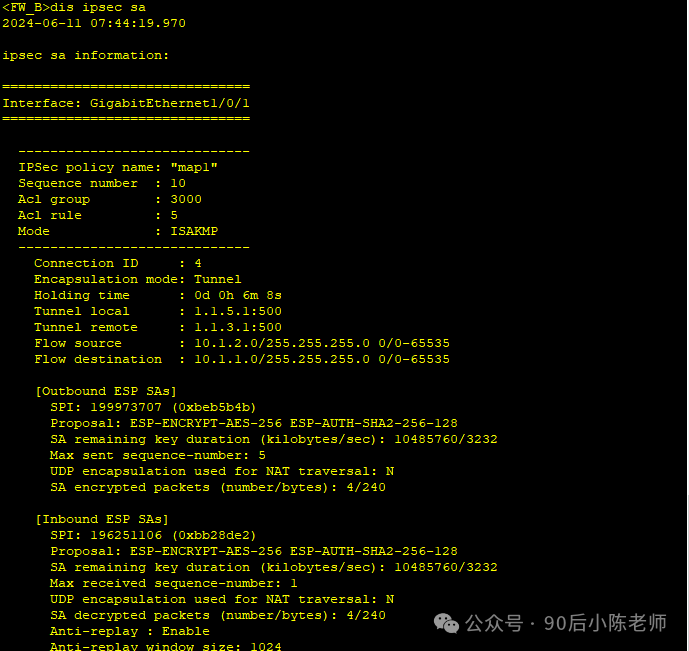
Брандмауэр Б
3. Полная настройка
Брандмауэр А
2024-06-11 07:45:45.660
!Software Version V500R005C10SPC300
#
sysname FW_A
#
l2tp domain suffix-separator @
#
undo info-center enable
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
update schedule location-sdb weekly Sun 00:12
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 04:26
update schedule av-sdb daily 04:26
update schedule sa-sdb daily 04:26
update schedule cnc daily 04:26
update schedule file-reputation daily 04:26
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
acl number 3000
rule 5 permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
#
ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer b
pre-shared-key %^%#)I56Q}{>TX>W[q'(ETN5x#YiJ`nZ#=YDn{<U(4(=%^%#
ike-proposal 10
remote-address 1.1.5.1
#
ipsec policy map1 10 isakmp
security acl 3000
ike-peer b
proposal tran1
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%aGq_:^(yHPG5l.*(Uw(Pw(jX<x'Q(O$;$7Q0FmB!5(u7(j[w@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%)YO^2z5%GIb]e8+JJ,o,a>x&%lJJ7.tkmBvY"%'E"2=N>x)a@%@%
level 15
manager-user admin
password cipher @%@%+nWr7W6$uC;w=iCvTBY2":,BCM$8>+whi;z_++;F1[9;:,E"@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 1.1.3.1 255.255.255.0
ipsec policy map1
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.1.1.1 255.255.255.0
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/3
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
#
ip route-static 1.1.5.0 255.255.255.0 1.1.3.2
ip route-static 10.1.2.0 255.255.255.0 1.1.3.2
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name policy1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 10.1.2.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.2.0 mask 255.255.255.0
action permit
rule name policy2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 1.1.3.1 mask 255.255.255.255
source-address 1.1.5.1 mask 255.255.255.255
destination-address 1.1.3.1 mask 255.255.255.255
destination-address 1.1.5.1 mask 255.255.255.255
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
returnБрандмауэр Б
2024-06-11 07:48:01.760
!Software Version V500R005C10SPC300
#
sysname FW_B
#
l2tp domain suffix-separator @
#
undo info-center enable
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
update schedule location-sdb weekly Sun 07:01
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 04:46
update schedule av-sdb daily 04:46
update schedule sa-sdb daily 04:46
update schedule cnc daily 04:46
update schedule file-reputation daily 04:46
#
ip vpn-instance default
<FW_B>save cu
<FW_B>save cu
^
Error: Wrong parameter found at '^' position.
<FW_B>
<FW_B>dis c
<FW_B>dis current-configuration
2024-06-11 07:48:15.200
!Software Version V500R005C10SPC300
#
sysname FW_B
#
l2tp domain suffix-separator @
#
undo info-center enable
#
ipsec sha2 compatible enable
#
undo telnet server enable
undo telnet ipv6 server enable
#
update schedule location-sdb weekly Sun 07:01
#
firewall defend action discard
#
banner enable
#
user-manage web-authentication security port 8887
undo privacy-statement english
undo privacy-statement chinese
page-setting
user-manage security version tlsv1.1 tlsv1.2
password-policy
level high
user-manage single-sign-on ad
user-manage single-sign-on tsm
user-manage single-sign-on radius
user-manage auto-sync online-user
#
web-manager security version tlsv1.1 tlsv1.2
web-manager enable
web-manager security enable
#
firewall dataplane to manageplane application-apperceive default-action drop
#
undo ips log merge enable
#
decoding uri-cache disable
#
update schedule ips-sdb daily 04:46
update schedule av-sdb daily 04:46
update schedule sa-sdb daily 04:46
update schedule cnc daily 04:46
update schedule file-reputation daily 04:46
#
ip vpn-instance default
ipv4-family
#
time-range worktime
period-range 08:00:00 to 18:00:00 working-day
#
acl number 3000
rule 5 permit ip source 10.1.2.0 0.0.0.255 destination 10.1.1.0 0.0.0.255
#
ipsec proposal tran1
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
ike proposal default
encryption-algorithm aes-256 aes-192 aes-128
dh group14
authentication-algorithm sha2-512 sha2-384 sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
ike proposal 10
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
ike peer a
pre-shared-key %^%#w,}EEs[rK/RlcsABt)~5n#9lOjthnCah}Q,uQ!/E%^%#
ike-proposal 10
remote-address 1.1.3.1
#
ipsec policy map1 10 isakmp
security acl 3000
ike-peer a
proposal tran1
#
aaa
authentication-scheme default
authentication-scheme admin_local
authentication-scheme admin_radius_local
authentication-scheme admin_hwtacacs_local
authentication-scheme admin_ad_local
authentication-scheme admin_ldap_local
authentication-scheme admin_radius
authentication-scheme admin_hwtacacs
authentication-scheme admin_ad
authorization-scheme default
accounting-scheme default
domain default
service-type internetaccess ssl-vpn l2tp ike
internet-access mode password
reference user current-domain
manager-user audit-admin
password cipher @%@%r^Jw!$61n0biZQ<~g[r97M{GZbSD,6(f;%fK7"XQkEBBM{J7@%@%
service-type web terminal
level 15
manager-user api-admin
password cipher @%@%fzvx<)h$WTbv&i4&bM(->];7EhiLN.wS>BDn%&J;O0hM];:>@%@%
level 15
manager-user admin
password cipher @%@%omb]SfI=d75[z]">~uo14p+T2R2HXp<8n!$9=4*R7#w!p+W4@%@%
service-type web terminal
level 15
role system-admin
role device-admin
role device-admin(monitor)
role audit-admin
bind manager-user audit-admin role audit-admin
bind manager-user admin role system-admin
#
l2tp-group default-lns
#
interface GigabitEthernet0/0/0
undo shutdown
ip binding vpn-instance default
ip address 192.168.0.1 255.255.255.0
alias GE0/METH
#
interface GigabitEthernet1/0/0
undo shutdown
#
interface GigabitEthernet1/0/1
undo shutdown
ip address 1.1.5.1 255.255.255.0
ipsec policy map1
#
interface GigabitEthernet1/0/2
undo shutdown
#
interface GigabitEthernet1/0/3
undo shutdown
ip address 10.1.2.1 255.255.255.0
#
interface GigabitEthernet1/0/4
undo shutdown
#
interface GigabitEthernet1/0/5
undo shutdown
#
interface GigabitEthernet1/0/6
undo shutdown
#
interface Virtual-if0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/3
#
firewall zone untrust
set priority 5
add interface GigabitEthernet1/0/1
#
firewall zone dmz
set priority 50
#
ip route-static 1.1.3.0 255.255.255.0 1.1.3.2
ip route-static 1.1.3.0 255.255.255.0 1.1.5.2
ip route-static 10.1.1.0 255.255.255.0 1.1.3.2
ip route-static 10.1.1.0 255.255.255.0 1.1.5.2
#
undo ssh server compatible-ssh1x enable
ssh authentication-type default password
ssh server cipher aes256_ctr aes128_ctr
ssh server hmac sha2_256 sha1
ssh client cipher aes256_ctr aes128_ctr
ssh client hmac sha2_256 sha1
#
firewall detect ftp
#
user-interface con 0
authentication-mode aaa
user-interface vty 0 4
authentication-mode aaa
protocol inbound ssh
user-interface vty 16 20
#
pki realm default
#
sa
#
location
#
multi-linkif
mode proportion-of-weight
#
right-manager server-group
#
device-classification
device-group pc
device-group mobile-terminal
device-group undefined-group
#
user-manage server-sync tsm
#
security-policy
rule name policy1
source-zone trust
source-zone untrust
destination-zone trust
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.0
source-address 10.1.2.0 mask 255.255.255.0
destination-address 10.1.1.0 mask 255.255.255.0
destination-address 10.1.2.0 mask 255.255.255.0
action permit
rule name policy2
source-zone local
source-zone untrust
destination-zone local
destination-zone untrust
source-address 1.1.3.0 mask 255.255.255.0
source-address 1.1.3.1 mask 255.255.255.255
source-address 1.1.5.1 mask 255.255.255.255
destination-address 1.1.3.1 mask 255.255.255.255
destination-address 1.1.5.1 mask 255.255.255.255
action permit
#
auth-policy
#
traffic-policy
#
policy-based-route
#
nat-policy
#
quota-policy
#
pcp-policy
#
dns-transparent-policy
#
rightm-policy
#
returnМаршрутизатор Р1
[V200R003C00]
#
sysname R1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface Ethernet0/0/0
#
interface Ethernet0/0/1
#
interface Ethernet0/0/2
#
interface Ethernet0/0/3
#
interface Ethernet0/0/4
#
interface Ethernet0/0/5
#
interface Ethernet0/0/6
#
interface Ethernet0/0/7
#
interface GigabitEthernet0/0/0
ip address 1.1.3.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 1.1.5.2 255.255.255.0
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
returnPC1
PC2
Учебное пособие по Jetpack Compose для начинающих, базовые элементы управления и макет

Код js веб-страницы, фон частицы, код спецэффектов

【новый! Суперподробное】Полное руководство по свойствам компонентов Figma.
🎉Обязательно к прочтению новичкам: полное руководство по написанию мини-программ WeChat с использованием программного обеспечения Cursor.
[Забавный проект Docker] VoceChat — еще одно приложение для мгновенного чата (IM)! Может быть встроен в любую веб-страницу!

Как реализовать переход по странице в HTML (html переходит на указанную страницу)

Как решить проблему зависания и низкой скорости при установке зависимостей с помощью npm. Существуют ли доступные источники npm, которые могут решить эту проблему?

Серия From Zero to Fun: Uni-App WeChat Payment Practice WeChat авторизует вход в систему и украшает страницу заказа, создает интерфейс заказа и инициирует запрос заказа

Серия uni-app: uni.navigateЧтобы передать скачок значения

Апплет WeChat настраивает верхнюю панель навигации и адаптируется к различным моделям.

JS-время конвертации

Обеспечьте бесперебойную работу ChromeDriver 125: советы по решению проблемы chromedriver.exe не найдены

Поле комментария, щелчок мышью, специальные эффекты, js-код
Объект массива перемещения объекта JS

Как открыть разрешение на позиционирование апплета WeChat_Как использовать WeChat для определения местонахождения друзей
Я даю вам два набора из 18 простых в использовании фонов холста Power BI, так что вам больше не придется возиться с цветами!

Получить текущее время в js_Как динамически отображать дату и время в js

Вам необходимо изучить сочетания клавиш vsCode для форматирования и организации кода, чтобы вам больше не приходилось настраивать формат вручную.

У ChatGPT большое обновление. Всего за 45 минут пресс-конференция показывает, что OpenAI сделал еще один шаг вперед.
Copilot облачной разработки — упрощение разработки
Микросборка xChatGPT с низким кодом, создание апплета чат-бота с искусственным интеллектом за пять шагов

CUDA Out of Memory: идеальное решение проблемы нехватки памяти CUDA
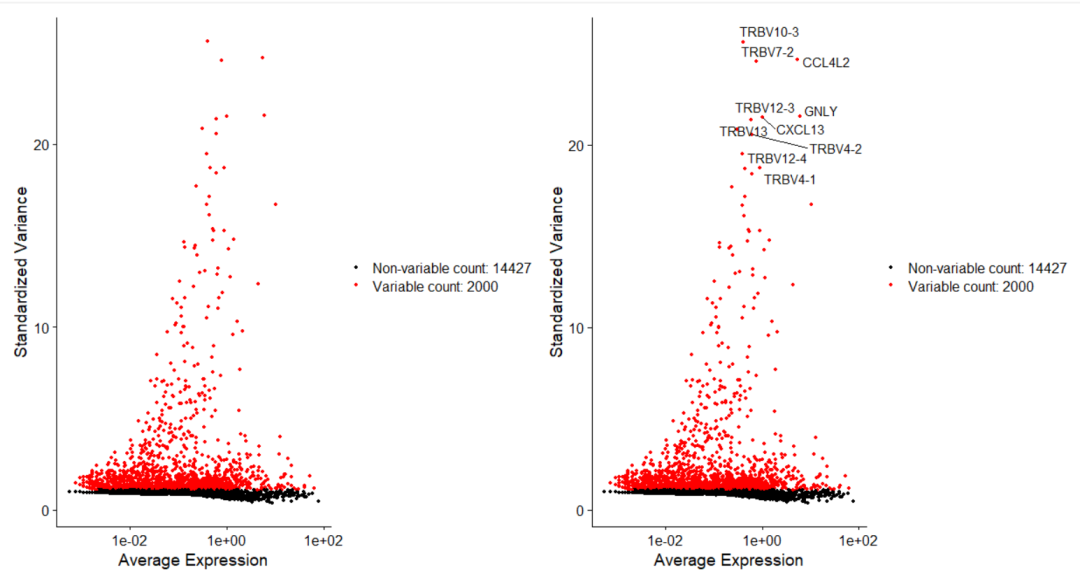
Анализ кластеризации отдельных ячеек, который должен освоить каждый&MarkerгенетическийВизуализация

vLLM: мощный инструмент для ускорения вывода ИИ

CodeGeeX: мощный инструмент генерации кода искусственного интеллекта, который можно использовать бесплатно в дополнение к второму пилоту.

Машинное обучение Реальный бой LightGBM + настройка параметров случайного поиска: точность 96,67%
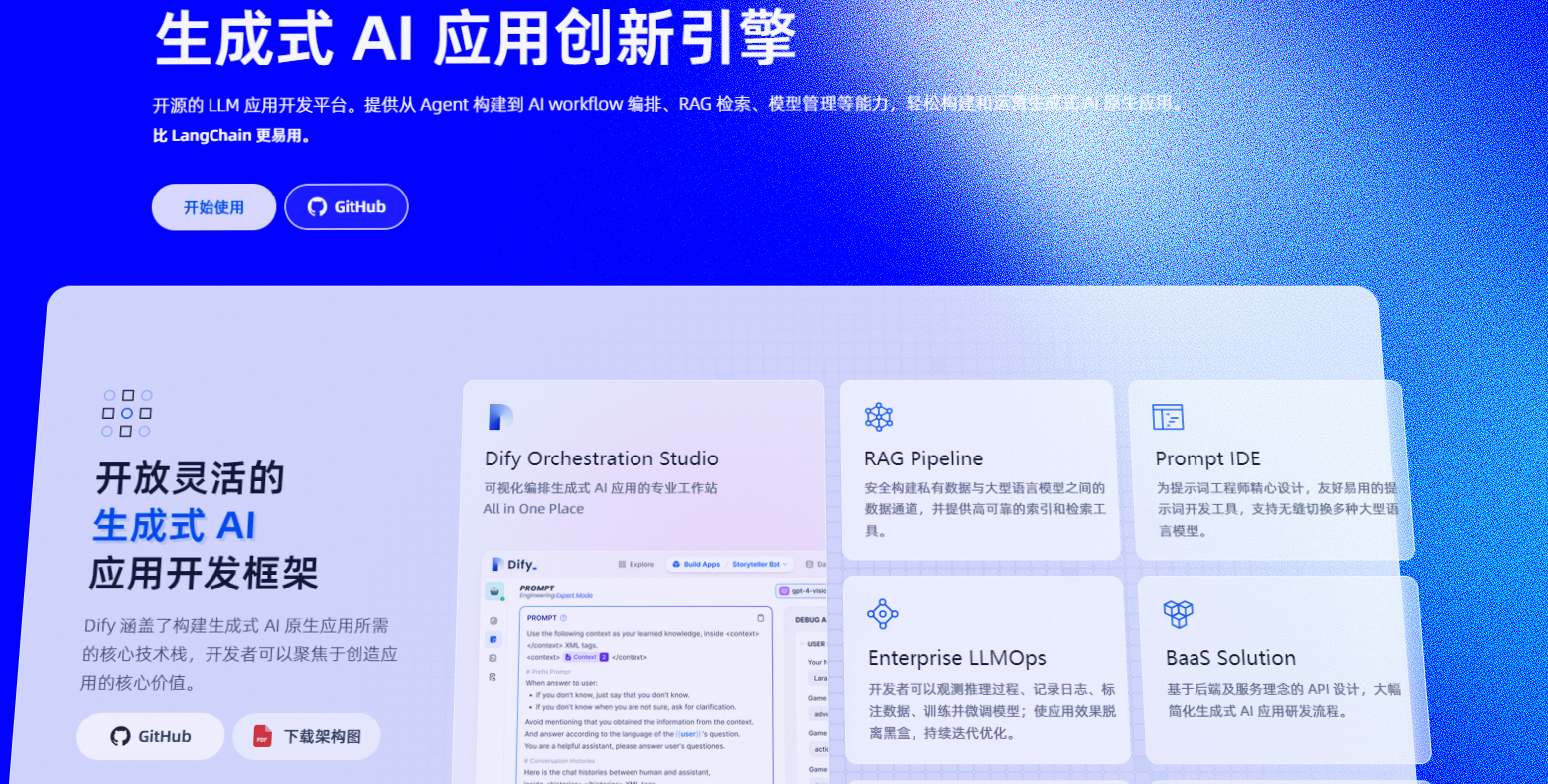
Бесшовная интеграция, мгновенный интеллект [1]: платформа больших моделей Dify-LLM, интеграция без кодирования и встраивание в сторонние системы, более 42 тысяч звезд, чтобы стать свидетелями эксклюзивных интеллектуальных решений.
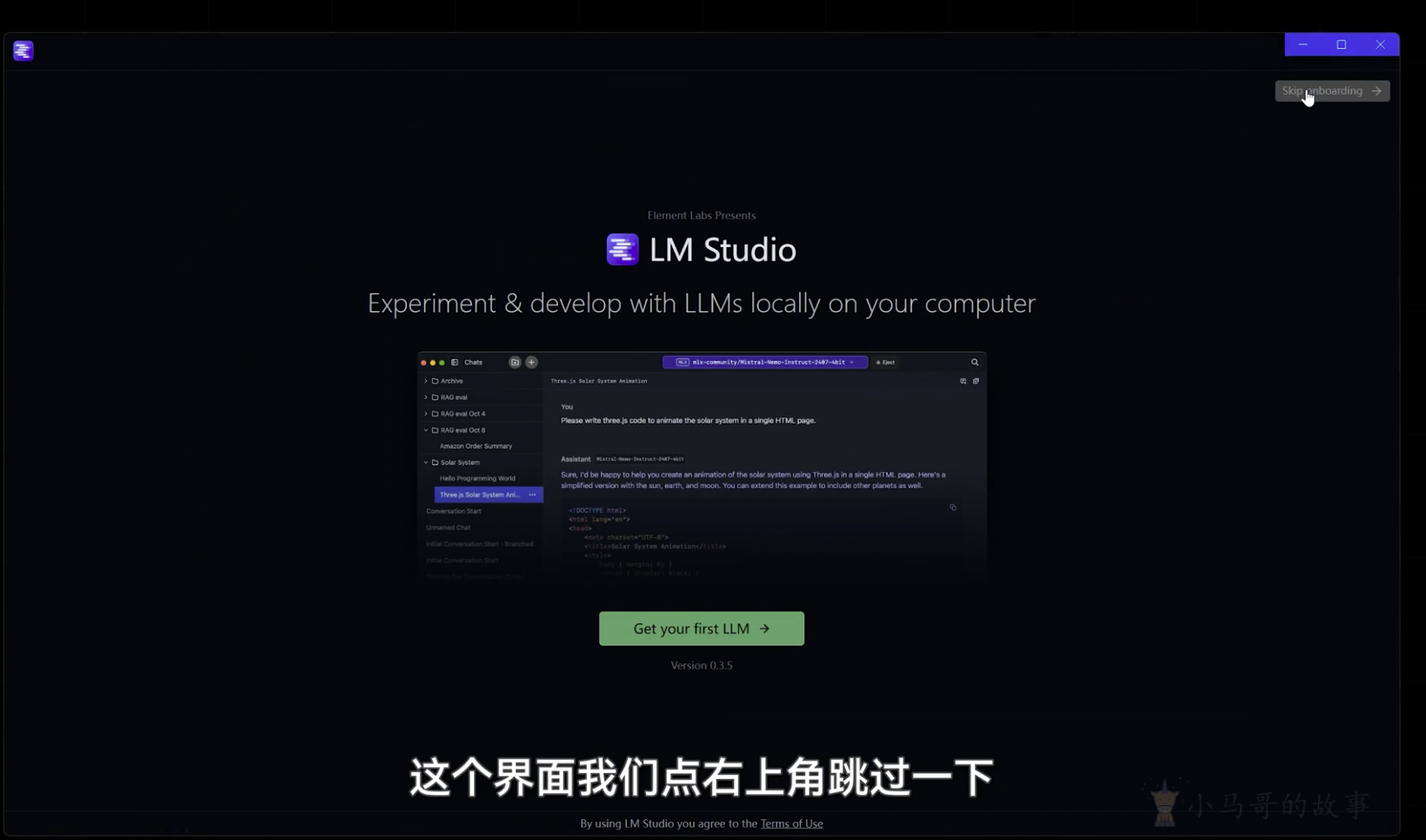
LM Studio для создания локальных больших моделей
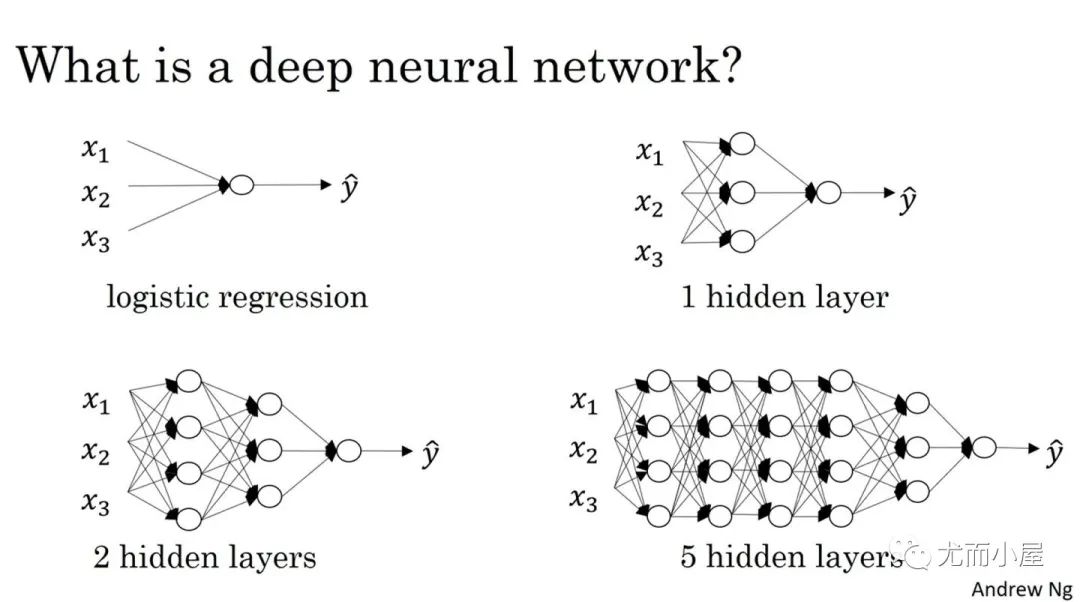
Как определить количество слоев и нейронов скрытых слоев нейронной сети?